WESETH® is a testing automation platform, expressly designed for cybersecurity verification of cyber-physical systems. WESETH® is designed to support the remote and automated validation of cybersecurity requirements and control on Benches, HIL or Proto Vehicles.
WESETH® Architecture
WESETH®’s high-security standards allow fully autonomous requirements verification as well as the integration of human experts in the loop for penetration testing.
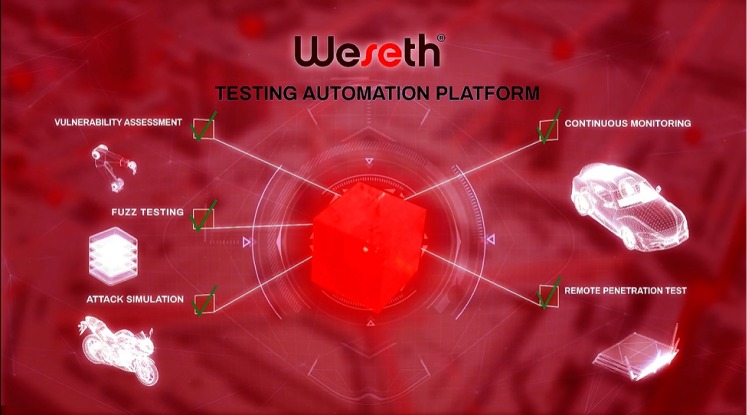
WESETH® Use Cases
WESETH® implements a wide variety of use cases including:
WESETH® part of CI/CD process
Build your internal Knowledge Base
WESETH® relies on DRIVESEC’s design test scripts database, which covers multiple attack scenarios and various requirements validation tools. Execution of those test scripts is made automatic by the support of the Weseth® platform execution mechanism.
Generation of new script
Drivesec has designed an initial set of scripts, which can be executed automatically on the WESETH BOX, to cover all the requirements indicated in Annex 5 of the UNECE R 155. This initial set of scripts covers attack simulation, systems and network fuzzing and requirements testing. The scripts database is a living object, and the number of scripts increases continuously based on the number of inputs.
Weseth® is simple and can be installed by no IT staff in a matter of 1 hour, without impacting on IT infrastructure.
Weseth® can be used to connect every type of systems with any type of interface, can be programmed and can support remote controls (through Digital I/O management).
Weseth® is fully managed and monitored to guarantee security, integrity and prevent tampering.
The features and the number of potential use cases supported by Weseth® are such that a comparison with another solution is too reductive.